This guide explains how to unlock a LUKS encrypted ubuntu system via SSH. This is convenient if in example you want to turn on a server but don't have a keyboard and screen attached to it. Or if you don't have physical access to it. I assume that you know already how to set up an OpenSSH server and you know how to activate/deactivate public key login. Else read Ubuntu Help: OpenSSH Server and check more online resources.
Debug1: sshexchangeidentification: Dropbear multi-purpose version 0.53.1. Debug1: sshexchangeidentification: Make a symlink pointing at this binary with one of the following names: debug1: sshexchangeidentification: 'dropbear' - the Dropbear server. Debug1: sshexchangeidentification: 'dbclient' or 'ssh' - the Dropbear client. Compatible with OpenSSH /.ssh/authorizedkeys public key authentication; The server, client, keygen, and key converter can be compiled into a single binary (like busybox) Features can easily be disabled when compiling to save space; Multi-hop mode uses SSH TCP forwarding to tunnel through multiple SSH hosts in a single command. So yourhost is the busybox router. Ssh -R 11111:nearhost:22 remotehost Now when you are at the remotehost, you type again. Ssh -p 11111 busyboxuser@localhost to connect to the green port 11111 which is then forwarded through the tunnel to the busybox, and from there it is connected to the pink port 22 of the nearhost (representing your home computer).
Feature Utilities; SSH: Dropbear has both an ssh server and an ssh client that together come in around 100k. It has no external dependencies (I.E. It does not depend on OpenSSL, using a built-in copy of LibTomCrypt instead). It's actively maintained, with a quiet but responsive mailing list.
This guide was tested with ubuntu 18.04 and ubuntu 17.10.
To connect from Windows, I used ssh from bash (if you install Git for Windows you get bash).
Open a terminal and install dropbear and busybox:
You will get a warning here as it completes: dropbear: WARNING: Invalid authorized_keys file, remote unlocking of cryptroot via SSH won't work!, just ignore it for now.
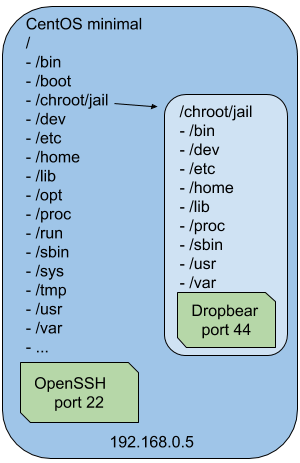
Activate BUSYBOX and DROPBEAR in initramfs
Change BUSYBOX=auto to option to BUSYBOX=y and add (below it or at the end of the file) this line:
Browse to the /etc/dropbear-initramfs/ directory, which includes all the dropbear configurations needed to be included in the initramfs:
Note: host keys are already present, as they were automatically generated during the installation of the dropbear package, so there is no need to create new ones as other guides tell you to do. Just convert the rsa one, as follows:
Add your client public key to the authorized_keys. If you are logged to your machine via SSH, and your public key is already in your authorized_keys file, you can copy the existing authorized_keys file, as follows:
Else you can add a public key as follows: sudo echo 'your public key' >> authorized_keys
Set dropbear to start:
Change NO_START=1 to NO_START=0
In dropbear, use a different port from the one you are using in your host, so you won't get the annoying 'man in the middle attack' warning in your ssh client that will notice that the host has different keys. Different ports are considered different hosts, so you won't get any warning at all. I've seen other complicated solutions to avoid the warning, but I think that using a different port is the easiest and most elegant solution.
Uncomment the DROPBEAR_OPTIONS line and add the option to specify the port. In this example I use port 21. Use the port you desire.
Now add the script that will be needed to actually unlock your LUKS partition:
Copy and paste the contents from gusennan' sh script in the file (or copy the text from the raw file), then give it executable rights:
Update initramfs:
Disable the dropbear service on boot, so it won't interfere with your openssh server:
Important, I had to update grub and disable the splash screen, because with splash active, after connecting to dropbear and typing unlock the screen was blocked and I could not enter the LUKS password.
In the GRUB_CMDLINE_LINUX_DEFAULT line, replace 'quiet slash' with 'quiet' , as follows:
Save and update grub:
Reboot your server:
Try to connect to your machine. You must use the root user, and specify the port you configured in the previous step:
Once connected you will see something like this:
type unlock , insert your LUKS password, if everything worked correctly your partition will decrypt and your machine will boot. You will see this:
Give it time to boot, then you can finally ssh into your linux box, as usual.
Encrypted HOME directory
If not only your partition is encrypted, but also your home directory, you won't be able to login with your public key, as the public key is saved in ~/.ssh/authorized_keys , which is encrypted.
To solve this, follow Stephen's Encrypted Home directories + SSH Key Authentication guide.
Troubleshooting
Busybox Ssh Server
If you get this error when you try to connect to your server, it's because you didn't follow my advise to change port in dropbear:I still prefer my solution, but if you insist on using the same port, here a few nerdy solutions:
Solution 1, works like a charm in linux, but not really on bash on windows.

Solution 2, provide some command line hack to avoid the warning:
Credits
This guide was inspired by:
Thanks also to Stephen (link above) for his encrypted home directories solution.
I hope that this guide was helpful for you, if so, consider buying a gadget at banggood using my referral link. Like this (comparing to a donation) we both benefit, you get a gadget that may be useful for you and I get something too (a little commission, but the price for you is the same).
Dropbear is a relatively small SSH server and client. It runs on a variety of POSIX-based platforms. Dropbear is particularly useful for 'embedded' type Linux systems.
- 1Enabling dropbear server
- 4Setting keys to get ssh connectivity without password requests
Enabling dropbear server
How to enable Dropbear server
1-Open sdk configuration system
2- Enable Dropbear server:
3- When Dropbear is selected, scp and ssh are showed
4- You should also enabled some user and password management tools
-> File System Configuration
Starting dropbear server
To start server, run the following script:
When this script run, normally the public key is printed in the log, similar to (long keys shortened to make it easier to ready):
Commands to use ssh
From target:

From host:
Commands to use scp
From target or host:
Example ssh client connecting to target hardware using a password
If something goes wrong while trying to connect to the dropbear ssh daemon, you can get some hints looking in /var/log/messages on the target file system.
On the target device:
On your host computer (adjust target hardware name/IP address as needed):
You should see something similar to the following if all is working correctly:
Adding root ssh login to development directory
If you always want the target file system to contain the same ssh keys and ability to use ssh to log in as root, run the steps above (using root NFS mount) and verify you can ssh in as root user, then:
These steps are useful when developing the product. You should delete the keys from the overlay file system before generating production code.
The above steps should not be used if more than one board will be on the same subnet as all boards will have the same ethernet MAC address.
Setting keys to get ssh connectivity without password requests
To enable this mode, add '-s' option at the start server command, it can be added in the devdir fs script or in the target fs directly.
To add this option in the devdir, open the file $DEVDIR/fs/apps/dropbear.x.y/dropbear and add the option '-s' in the flag DROPBEAR_EXTRA_ARGS
After do that, rebuild and reinstall the application, then start the Dropbear server running the following script:
The first time that this script run, the script prints in log the public key. If Dropbear was started at this point, the public key can be print it manually, this process must be explained in the next section.
To add this option in the target fs directly, repeat the same action in the script /etc/init.d/dropbear. After that, restart the application
How to get Dropbear public and private keys in target manually
The 'dropbearkey' tool creates public and private keys or show the public key.
To create an pair of keys, run the following command:

The last command saves in /etc/dropbear/dropbear_rsa_host_key the private key, and prints the public key. To show only the public key in the required format, run the commmand:
How to set Dropbear public key in host
When the public key was generated by Dropbear in the target, it must be added in the correctly host file location.
The public key must added in the file
The public key generated by Dropbear must have similar format to:
After to add the public key in the host, reinitialize the ssh server:
How to get OpenSSH public and private keys in host computer (dsa)
You need to create a public / private key and install the public key on the target file system.
On your host computer:
There are two options for installing the public key on the target file system.
If you are using $DEVDIR/myapps/fs_overlay:
Otherwise, just install the public key directly into the SDK target file system directory:
In both cases you need to make sure the owner and group for the .ssh directory and .ssh/authorized_keys is set correctly from the target device's point of view.
On your host computer, verify you can ssh to target hardware without using a password:
You need to create a public / private key and install the public key on the target file system.
On your host computer:
There are two options for installing the public key on the target file system.
If you are using $DEVDIR/myapps/fs_overlay:
Otherwise, just install the public key directly into the SDK target file system directory:
In both cases you need to make sure the owner and group for the .ssh directory and .ssh/authorized_keys is set correctly from the target device's point of view.
Busybox Ssh Server Ip
On your host computer, verify you can ssh to target hardware without using a password:
How to get OpenSSH public and private keys in host computer (ras)
The following command, creates two files in ~/.ssh/, one is named id_rsa and is the private key (It mustn't be touched) and other that is named id_rsa.pub, this file contain the public key, this content must be added in target location explained in the next section.
How to set OpenSSH public key in target
The public key generated in host, must be added in the target file /home//.ssh/authorized_keys, It must have format similar to:
Set the permissions correctly
Busybox Ssh Client
After to do that, restart the Dropbear server using the following command:
Commands to use ssh without password request
From host:

Activate BUSYBOX and DROPBEAR in initramfs
Change BUSYBOX=auto to option to BUSYBOX=y and add (below it or at the end of the file) this line:
Browse to the /etc/dropbear-initramfs/ directory, which includes all the dropbear configurations needed to be included in the initramfs:
Note: host keys are already present, as they were automatically generated during the installation of the dropbear package, so there is no need to create new ones as other guides tell you to do. Just convert the rsa one, as follows:
Add your client public key to the authorized_keys. If you are logged to your machine via SSH, and your public key is already in your authorized_keys file, you can copy the existing authorized_keys file, as follows:
Else you can add a public key as follows: sudo echo 'your public key' >> authorized_keys
Set dropbear to start:
Change NO_START=1 to NO_START=0
In dropbear, use a different port from the one you are using in your host, so you won't get the annoying 'man in the middle attack' warning in your ssh client that will notice that the host has different keys. Different ports are considered different hosts, so you won't get any warning at all. I've seen other complicated solutions to avoid the warning, but I think that using a different port is the easiest and most elegant solution.
Uncomment the DROPBEAR_OPTIONS line and add the option to specify the port. In this example I use port 21. Use the port you desire.
Now add the script that will be needed to actually unlock your LUKS partition:
Copy and paste the contents from gusennan' sh script in the file (or copy the text from the raw file), then give it executable rights:
Update initramfs:
Disable the dropbear service on boot, so it won't interfere with your openssh server:
Important, I had to update grub and disable the splash screen, because with splash active, after connecting to dropbear and typing unlock the screen was blocked and I could not enter the LUKS password.
In the GRUB_CMDLINE_LINUX_DEFAULT line, replace 'quiet slash' with 'quiet' , as follows:
Save and update grub:
Reboot your server:
Try to connect to your machine. You must use the root user, and specify the port you configured in the previous step:
Once connected you will see something like this:
type unlock , insert your LUKS password, if everything worked correctly your partition will decrypt and your machine will boot. You will see this:
Give it time to boot, then you can finally ssh into your linux box, as usual.
Encrypted HOME directory
If not only your partition is encrypted, but also your home directory, you won't be able to login with your public key, as the public key is saved in ~/.ssh/authorized_keys , which is encrypted.
To solve this, follow Stephen's Encrypted Home directories + SSH Key Authentication guide.
Troubleshooting
Busybox Ssh Server
If you get this error when you try to connect to your server, it's because you didn't follow my advise to change port in dropbear:I still prefer my solution, but if you insist on using the same port, here a few nerdy solutions:
Solution 1, works like a charm in linux, but not really on bash on windows.
Overview DBeaver EE supports MongoDB schema browser, data viewer, SQL and JavaScript queries execution. Also it supports various administrative tools (like server sessions manager). DBeaver uses MongoDB Java driver 3.8.0 to operate with server.
Solution 2, provide some command line hack to avoid the warning:
Credits
This guide was inspired by: https://oliverviebrooks.com/2017/12/05/unlocking-luks-volumes-without-local-access/
Thanks also to Stephen (link above) for his encrypted home directories solution.
I hope that this guide was helpful for you, if so, consider buying a gadget at banggood using my referral link. Like this (comparing to a donation) we both benefit, you get a gadget that may be useful for you and I get something too (a little commission, but the price for you is the same).
Dropbear is a relatively small SSH server and client. It runs on a variety of POSIX-based platforms. Dropbear is particularly useful for 'embedded' type Linux systems.
- 1Enabling dropbear server
- 4Setting keys to get ssh connectivity without password requests
Enabling dropbear server
How to enable Dropbear server
1-Open sdk configuration system
2- Enable Dropbear server:
3- When Dropbear is selected, scp and ssh are showed
4- You should also enabled some user and password management tools
-> File System Configuration
Starting dropbear server
To start server, run the following script:
When this script run, normally the public key is printed in the log, similar to (long keys shortened to make it easier to ready):
Commands to use ssh
From target:
From host:
Commands to use scp
From target or host:
Example ssh client connecting to target hardware using a password
If something goes wrong while trying to connect to the dropbear ssh daemon, you can get some hints looking in /var/log/messages on the target file system.
On the target device:
On your host computer (adjust target hardware name/IP address as needed):
You should see something similar to the following if all is working correctly:
Adding root ssh login to development directory
If you always want the target file system to contain the same ssh keys and ability to use ssh to log in as root, run the steps above (using root NFS mount) and verify you can ssh in as root user, then:
These steps are useful when developing the product. You should delete the keys from the overlay file system before generating production code.
The above steps should not be used if more than one board will be on the same subnet as all boards will have the same ethernet MAC address.
Setting keys to get ssh connectivity without password requests
To enable this mode, add '-s' option at the start server command, it can be added in the devdir fs script or in the target fs directly.
To add this option in the devdir, open the file $DEVDIR/fs/apps/dropbear.x.y/dropbear and add the option '-s' in the flag DROPBEAR_EXTRA_ARGS
After do that, rebuild and reinstall the application, then start the Dropbear server running the following script:
The first time that this script run, the script prints in log the public key. If Dropbear was started at this point, the public key can be print it manually, this process must be explained in the next section.
To add this option in the target fs directly, repeat the same action in the script /etc/init.d/dropbear. After that, restart the application
How to get Dropbear public and private keys in target manually
The 'dropbearkey' tool creates public and private keys or show the public key.
To create an pair of keys, run the following command:
The last command saves in /etc/dropbear/dropbear_rsa_host_key the private key, and prints the public key. To show only the public key in the required format, run the commmand:
How to set Dropbear public key in host
When the public key was generated by Dropbear in the target, it must be added in the correctly host file location.
The public key must added in the file
The public key generated by Dropbear must have similar format to:
After to add the public key in the host, reinitialize the ssh server:
How to get OpenSSH public and private keys in host computer (dsa)
You need to create a public / private key and install the public key on the target file system.
On your host computer:
There are two options for installing the public key on the target file system.
If you are using $DEVDIR/myapps/fs_overlay:
Otherwise, just install the public key directly into the SDK target file system directory:
In both cases you need to make sure the owner and group for the .ssh directory and .ssh/authorized_keys is set correctly from the target device's point of view.
On your host computer, verify you can ssh to target hardware without using a password:
You need to create a public / private key and install the public key on the target file system.
On your host computer:
There are two options for installing the public key on the target file system.
If you are using $DEVDIR/myapps/fs_overlay:
Otherwise, just install the public key directly into the SDK target file system directory:
In both cases you need to make sure the owner and group for the .ssh directory and .ssh/authorized_keys is set correctly from the target device's point of view.
Busybox Ssh Server Ip
On your host computer, verify you can ssh to target hardware without using a password:
How to get OpenSSH public and private keys in host computer (ras)
The following command, creates two files in ~/.ssh/, one is named id_rsa and is the private key (It mustn't be touched) and other that is named id_rsa.pub, this file contain the public key, this content must be added in target location explained in the next section.
How to set OpenSSH public key in target
The public key generated in host, must be added in the target file /home//.ssh/authorized_keys, It must have format similar to:
Set the permissions correctly
Busybox Ssh Client
After to do that, restart the Dropbear server using the following command:
Commands to use ssh without password request
From host:
From target:
Commands to use scp without password request
Form host:
Busybox Ssh Server Download
Form target:
Busybox Linux
There is more information about Remote Access.

